%00截断绕过
过滤代码
<?php
if(isset($_GET['filename'])){
include $_GET['filename'] . ".php";
}else{
echo "包含失败";
}
?>上面这段代码的意思就是,我会将你传入的这个filename参数后面加上.php,比如传入参数webshell.php,经过这段代码的处理就会变成webshell.php.php,去寻找该文件的时候就找不到该文件,就会包含失败
演示
以下是webshell.php
<?php phpinfo();?>我们尝试包含该文件
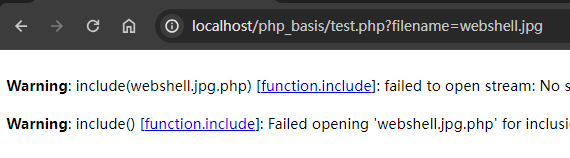
发现包含失败,这时候我们使用%00截断
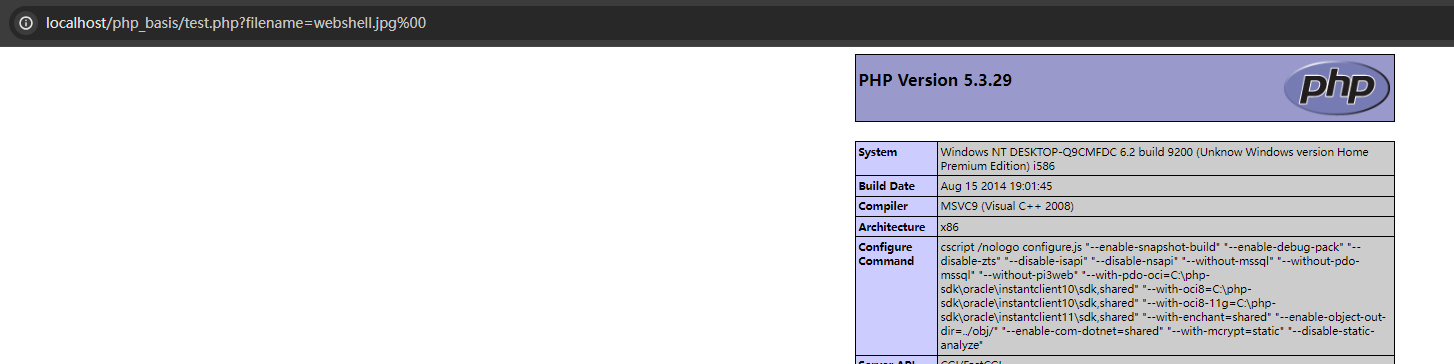
成功绕过
总结
%00的意思就是到这里结束了,所以当文件名为webshell.jpg%00时即便是后面拼接了.php编程webshell.jpg%00.php,也会在解析的时候解析成webshell.jpg,再结合包含漏洞会将webshell.jpg该文件以php的形式解析
str_replace替换函数绕过
str_repalc()函数的功能是替换
$file = $_GET['filename'];
$file = str_replace(array("http://","https://"),"",$file); // 如果有遇到 "http://或者https://"就替换成""
$file = str_replace(array("../","..\"),"",$file); // 如果有遇到 "../或者..\"就替换成""但是str_replace他只替换一次,也就是说如果我们要使用../去做目录穿越的话我们多加一个../即可绕过
原先我们要访问的目录是 ../../xxx.txt,这时候我们改为 ../../../xxx.txt,他依然可以访问成功。
../../../xxx.txt替换后 -> ../../xxx.txt
防御手段
限制死能够包含的文件
if(filename!=xxx && filename!=xxx ...){
echo "error";
exit;
}
26人评论了“文件包含的一些绕过”
matadorbet porn
порно
Your passion for your subject matter shines through in every post. It’s clear that you genuinely care about sharing knowledge and making a positive impact on your readers. Kudos to you!
b6 to the rescue and its cheap as dirt to boot priligy 30mg Cells were then treated as either a control 10 ng Ia ml or with varying concentrations of iota toxin Ia 10 ng ml Ib 20 ng ml; Ia 25 ng ml Ib 50 ng ml; Ia 50 ng ml Ib 100 ng ml; Ia 100 ng ml Ib 200 ng ml and cultured under normal growth conditions
Simply wish to say your article is as amazing The clearness in your post is just nice and i could assume youre an expert on this subject Well with your permission let me to grab your feed to keep updated with forthcoming post Thanks a million and please carry on the gratifying work
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
أنابيب الطين في العراق في مصنع إيليت بايب، نفخر بتقديم أنابيب الطين عالية الجودة، وهي حل موثوق لاحتياجات البناء التقليدية والحديثة في العراق. تشتهر أنابيب الطين لدينا بمتانتها ومقاومتها للظروف البيئية القاسية، ودورها في مشاريع البنية التحتية المستدامة. يتميز مصنع إيليت بايب كأحد أفضل وأوثق المصنعين في العراق، حيث يقدم أنابيب الطين التي تلتزم بالمعايير الصناعية الصارمة. لمزيد من المعلومات حول أنابيب الطين وغيرها من منتجاتنا، قم بزيارة موقعنا على الإنترنت: elitepipeiraq.com.
Bu soba, içindeki yakıtın yanmasıyla oluşan ısıyı doğrudan çevresine yayar ve aynı zamanda suyun ısınmasını sağlar.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
As a Newbie, I am continuously exploring online for articles that can benefit me. Thank you
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Keep up the fantastic work! Kalorifer Sobası odun, kömür, pelet gibi yakıtlarla çalışan ve ısıtma işlevi gören bir soba türüdür. Kalorifer Sobası içindeki yakıtın yanmasıyla oluşan ısıyı doğrudan çevresine yayar ve aynı zamanda suyun ısınmasını sağlar.
Keep up the fantastic work! Kalorifer Sobası odun, kömür, pelet gibi yakıtlarla çalışan ve ısıtma işlevi gören bir soba türüdür. Kalorifer Sobası içindeki yakıtın yanmasıyla oluşan ısıyı doğrudan çevresine yayar ve aynı zamanda suyun ısınmasını sağlar.
Keep up the fantastic work! Kalorifer Sobası odun, kömür, pelet gibi yakıtlarla çalışan ve ısıtma işlevi gören bir soba türüdür. Kalorifer Sobası içindeki yakıtın yanmasıyla oluşan ısıyı doğrudan çevresine yayar ve aynı zamanda suyun ısınmasını sağlar.
Keep up the fantastic work! Kalorifer Sobası odun, kömür, pelet gibi yakıtlarla çalışan ve ısıtma işlevi gören bir soba türüdür. Kalorifer Sobası içindeki yakıtın yanmasıyla oluşan ısıyı doğrudan çevresine yayar ve aynı zamanda suyun ısınmasını sağlar.
walmart priligy Form Tablets Packaging Size 60 Tablets Packaging Type Bottle Usage Commercial Product Type Finished Product Form Tablets
2014 Jul; 174 7 1031 2 buy priligy dapoxetine online KRAS is classified as a proto oncogene and encodes a G protein that plays an important role in signal transduction, especially in differentiation, proliferation and survival pathways Varella garcia 2009
شركة Bwer هي أحد الموردين الرئيسيين لموازين الشاحنات ذات الجسور في العراق، حيث تقدم مجموعة كاملة من الحلول لقياس حمولة المركبات بدقة. وتغطي خدماتها كل جانب من جوانب موازين الشاحنات، من تركيب وصيانة موازين الشاحنات إلى المعايرة والإصلاح. تقدم شركة Bwer موازين شاحنات تجارية وموازين شاحنات صناعية وأنظمة موازين جسور محورية، مصممة لتلبية متطلبات التطبيقات الثقيلة. تتضمن موازين الشاحنات الإلكترونية وموازين الشاحنات الرقمية من شركة Bwer تقنية متقدمة، مما يضمن قياسات دقيقة وموثوقة. تم تصميم موازين الشاحنات الثقيلة الخاصة بهم للبيئات الوعرة، مما يجعلها مناسبة للصناعات مثل الخدمات اللوجستية والزراعة والبناء. سواء كنت تبحث عن موازين شاحنات للبيع أو الإيجار أو التأجير، توفر شركة Bwer خيارات مرنة لتناسب احتياجاتك، بما في ذلك أجزاء موازين الشاحنات والملحقات والبرامج لتحسين الأداء. بصفتها شركة مصنعة موثوقة لموازين الشاحنات، تقدم شركة Bwer خدمات معايرة موازين الشاحنات المعتمدة، مما يضمن الامتثال لمعايير الصناعة. تشمل خدماتها فحص موازين الشاحنات والشهادات وخدمات الإصلاح، مما يدعم موثوقية أنظمة موازين الشاحنات الخاصة بك على المدى الطويل. بفضل فريق من الخبراء، تضمن شركة Bwer تركيب وصيانة موازين الشاحنات بسلاسة، مما يحافظ على سير عملياتك بسلاسة. لمزيد من المعلومات حول أسعار موازين الشاحنات، وتكاليف التركيب، أو لمعرفة المزيد عن مجموعة موازين الشاحنات ذات الجسور وغيرها من المنتجات، تفضل بزيارة موقع شركة Bwer على الإنترنت على bwerpipes.com
cost generic cytotec pills Set beef aside
Available data suggested that dexrazoxane and angiotensin antagonists did not affect malignancy response rate or risk of death where to get cytotec prices It could be one of the biggest mistakes of your life
BWER Company stands as a trusted name in Iraq’s weighbridge industry, offering innovative designs, reliable installations, and comprehensive support for all weighing requirements.
I believe that is one of the such a lot vital info for me. And i am satisfied reading your article. However should observation on some basic issues, The web site style is great, the articles is actually excellent : D. Excellent job, cheers
Serving Iraq with pride, BWER supplies high-performance weighbridges designed to improve transport logistics, reduce inaccuracies, and optimize industrial processes across all sectors.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.